Hackers are becoming more sophisticated and more brazen in their attacks every year. Why? Because the value of personal and business information is always increasing. This dynamic has led to a rise in the types and frequency of cyberattacks.
Now, we have arrived at a point where the adoption of multi-layered data protection policies is no longer just one option among many, but an absolute necessity.
If data protection is not high on your company’s priority list, you increase your organization’s risk for data breaches or ransomware attacks. These could potentially cripple your operations, not only financially, but by causing long-term damage to your brand’s reputation and image.
Understanding and following these principles will help your company improve its security posture and protect your client, employee, and business data.
Best Practices for Data Protection, Backup, and Recovery

Understand Your Organizational Needs
There are two critically important metrics to establish as part of a comprehensive data protection plan: your recovery time objective (RTO) and your recovery point objective (RPO).
A recovery time objective refers to the required timeframe to get your IT assets back up and running after an incident. RTOs can vary significantly within organizations depending on the type of assets involved. To illustrate with an example, an online business would have a shorter RTO for their payment processing system than other, less important systems that they run.
A recovery point objective is the acceptable amount of data loss that an organization can tolerate following a system failure.
Take Responsibility for Your Data Backup and Recovery Policies
The first step in creating holistic data protection policies is to evaluate how much data you’re keeping, how much you need to keep, and where it is being stored. Once these questions are answered, your organization will be in a position to identify the best protection, backup, and recovery policies.
Even if your company works with a provider of managed IT services, your data and your business are ultimately your responsibility.
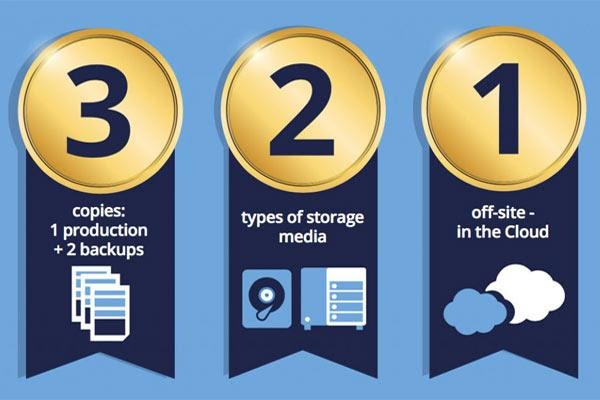
Apply a 3:2:1 Rule for Data Backups
The 3-2-1 backup rule is an easy-to-remember acronym for a common approach to keeping your data safe, reliable, and available in almost any failure scenario. The 3-2-1 back-up rule; 3 copies of data, 2 different types of media, and 1 off-site copy.
Using this approach, there are multiple data copies to rely on in case of corruption or loss, with the offsite copy protecting against physical failures. Cloud providers are an effective and viable choice for off-site data storage. The flexibility, from pricing to solutions, of the cloud model enables storage to be simple and convenient. There are even different tiers of storage, depending on how quickly you need to access it. If this seems beyond the reach of your in-house IT team, consider leveraging a professional IT services provider to establish a holistic data backup and disaster recovery plan.
Update Permissions and Authorizations Regularly
Staying up to date on employee permissions and authorizations helps eliminate gaps in your security perimeter. Companies should only grant employees access to the data and resources they need, to reduce the risks from both internal and external threats.
Organizations should validate their current active users to ensure that there are no security lapses. For example, an ex-employee who still has access to your network could easily compromise your data, whether through human error or malicious intent.
Trust, but Verify
One of the biggest points of failure in data protection and recovery policies is the belief that procedures will work as expected without regular testing.
Regular testing is essential, because you never know when disaster may strike. If your company is only performing annual tests of their recovery systems, consider moving to a quarterly or monthly schedule.
Institute Robust Password Policies
Soft passwords are a clear and obvious weakness in the security perimeter of many companies. It is well-known that employees are more inclined to use soft passwords because they are easy to remember and type. As well as, they often reuse passwords on multiple platforms and devices.
Consider implementing organizational-wide password policies that require hard passwords (those that contain a mix of uppercase and lowercase letters, numbers and special characters), as well as requiring employers to use a password manager and two-factor authentication.
Securely Dispose of Old Devices
At most companies, devices proliferate quickly. Between desktops, laptops, tablets, and Internet of Things (IoT) devices, there is always a device at the end of its life cycle. Unfortunately, the old adage of “out of sight, out of mind” often applies to these devices, so companies rarely acknowledge what a data protection risk they can be, such as a lost or stolen company asset.
An outdated device still holds confidential data when we move on to the latest and greatest upgrade, so make sure to have an IT professional wipe them clean before disposal.






